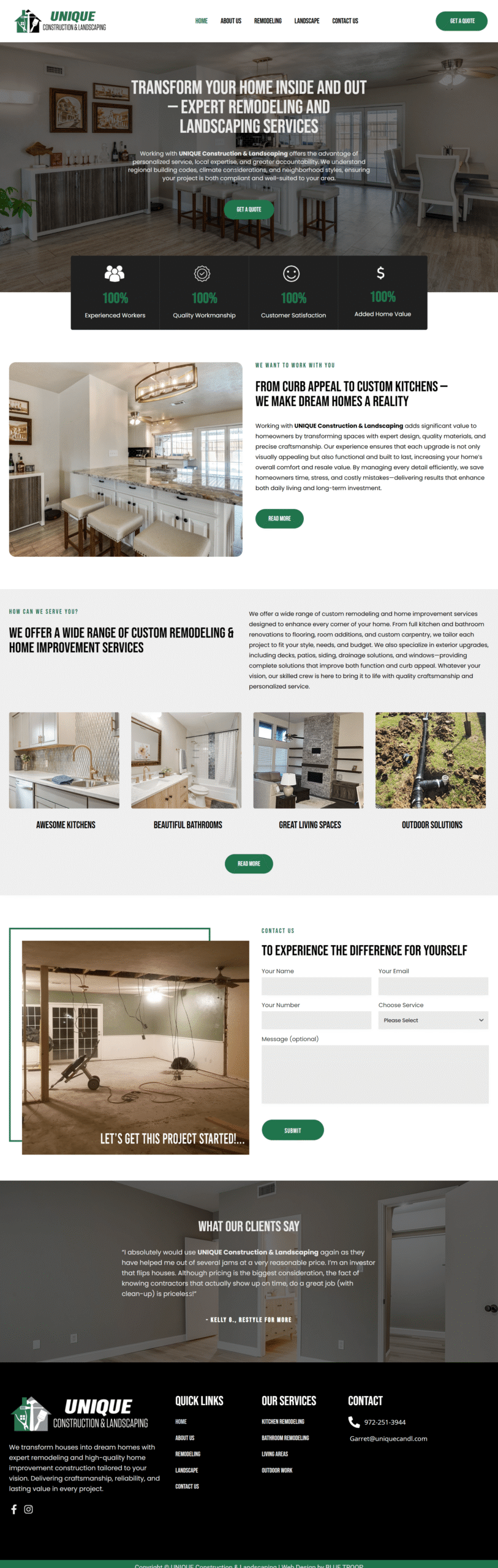
Overview
The JavaScript ecosystem faced a major security scare recently when a malicious set of NPM packages compromised thousands of React.js and Next.js applications. This incident highlights how modern frontend development—especially for React and Next.js—can be vulnerable to supply-chain attacks. If your business depends on web development, or you’re a developer working with JavaScript frameworks, this is an attack you absolutely need to know about.
What Was the Recent React/Next.js Attack?
In late 2024, security researchers uncovered several malicious NPM packages intentionally designed to target React.js and Next.js projects.
These packages:
-
had names similar to popular React/Next utilities
-
looked completely safe
-
were installed by thousands of developers
-
executed hidden scripts during installation
These hidden scripts collected:
All collected data was quietly sent to remote servers controlled by attackers.
This was a real supply-chain attack, not a theoretical vulnerability.
Why React.js & Next.js Projects Were Impacted
React and Next.js rely heavily on NPM packages. Most Next.js projects run server-side builds where sensitive data (like environment variables) is accessible.
This means any malicious package can:
In short, the attack exploited:
How the Attack Was Discovered
A developer noticed unusual outbound network requests during a next build. After investigating, he found:
The malicious packages were removed from NPM soon after, but many applications had already been built and deployed using them.
If You Use React or Next.js, You Should Care
Even if your project was not affected, this incident is a serious warning. Most React/Next developers install packages without much verification. If you’ve ever run:
…you could easily install a harmful package without knowing.
Businesses using React or Next.js for:
-
eCommerce
-
CRMs
-
Internal dashboards
-
SaaS apps
-
Booking platforms
are all vulnerable when supply-chain attacks target JavaScript dependencies.
How to Check If Your Project Was Affected
Here’s a simple checklist for your team:
Review package.json
Look for dependencies you don’t recognize.
Verify package authors, downloads, and GitHub links
Suspicious signs include:
Check for hidden post-install scripts
Malicious packages often hide scripts like:
"scripts": {
"postinstall": "node hidden-script.js"
}
Rotate your API keys
If you installed a suspicious dependency, assume your secrets were exposed.
Enable automated security monitoring
Use tools such as:
-
Snyk
-
Dependabot
-
npm audit
How to Protect React/Next.js Apps Going Forward
This attack showed how fragile the JavaScript ecosystem can be — but securing your apps is manageable.
1. Use trusted libraries only
Avoid unknown packages. Prefer libraries with:
-
history
-
active maintenance
-
verified authors
2. Lock versions and use package-lock.json
This prevents unexpected updates from pulling malicious code.
3. Run audits regularly
4. Add security scanning to CI/CD
Let your pipeline block vulnerable packages before deployment.
5. Reduce dependency bloat
The fewer dependencies you install, the smaller your attack surface.
Final Thoughts
This attack wasn’t caused by flaws in React or Next.js. It was a reminder that the JavaScript ecosystem is massive, open, and sometimes risky. With thousands of packages available, attackers need only one malicious release to cause widespread impact.
The best protection is awareness.
If you’re building or managing React/Next.js applications, take this incident seriously and strengthen your security practices now — before the next attack happens.
We will analyze your dependencies, APIs, authentication flow, and build pipeline to ensure your project is protected from supply-chain threats.
Protect your code. Protect your users. Protect your business.